iCloud and Password Security
The issue of cloud security has exploded over the past couple of weeks following the leak of private photos of more than 100 female celebrities, with Hunger Games actress Jennifer Lawrence at the forefront of the scandal. As well as igniting a debate surrounding privacy and internet censorship, Apple’s iCloud service has come under scrutiny following initial claims that a vulnerability in the system was the cause of the leak.
The iCloud service allows users to store photos, videos, music and other content and access it from their phones. Users can also choose to automatically backup their camera roll, with photos appearing seconds after you’ve snapped them. Cloud security – on the user and company’s side – has been a massive concern since the technology started to gain prominence over the last decade. But, obviously, that hasn’t stopped the rapid adoption of services like iCloud and Dropbox, offering reams of storage and allowing users to access their files from multiple devices, all over the world.

Apple’s ‘Find my iPhone’, like all other Apple services, uses a user’s Apple ID and password; but, unlike iTunes and iMail, their iPhone-finding service has no limit on the number of times an incorrect password can be entered. Or at least, it did until Apple released a patch, fuelling rumours that this was the way the hacker got in. Malicious ‘brute force’ programs can repeatedly guess random passwords for a given usernames, until they get the right one.
Almost immediately, Apple responded with a statement saying “we take user privacy very seriously and are actively investigating this report”, as well as patching the Find my iPhone exploit as a pre-emptive measure. Despite Apple’s hurried patch of this exploit, cracks in this theory started to appear. How did the usernames get into the hands of the hacker? Why did the victims not get security notifications that appear if your iCloud account is logged into on a new device? Why did many of the images reveal in the meta data that they were taken with Android phones and Canon cameras?
Sure enough, after two days, Apple presented the findings of their investigation – the photos did originate from iCloud, but the accounts weren’t accessed as a result of an exploit in Find my iPhone. Instead, this was a targeted attack. In their statement, they said "After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple's systems including iCloud or Find my iPhone”. In short, the celebrities’ iCloud accounts were accessed by weak passwords or weak security questions, as well as a failure to enable additional security in the form of a ‘two-step’ verification. Two-step verifications require an additional, second password to be entered, in the form of a PIN, which is sent via text. Lots of online services, including PayPal, Google, Facebook and Twitter, give the option for users to utilise this feature; the problem is, people are often reluctant to use it due to the perceived hassle and unwillingness to hand over their mobile number.
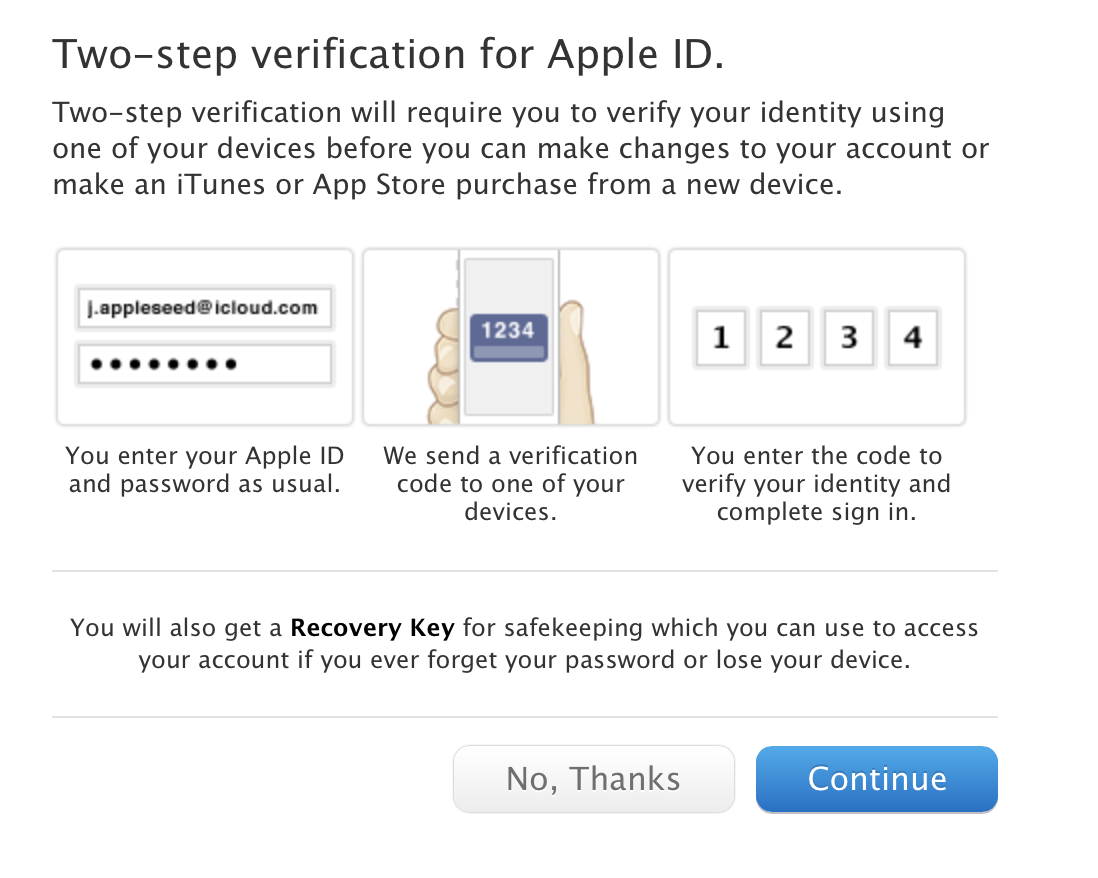
Nonetheless, Apple’s SEO Tim Cook has announced that additional security measures will be bought in, namely a new and improved notifications system that informs users when their data may be being compromised. The main new feature that is due to be rolled out within the next few weeks is an alert if someone tries to download your iCloud backup, something which doesn’t currently happen. Apple are also going to actively encourage people to use the two-step verification system. Cook, however, pointed out that Apple can make all the changes in the world but all this does is merely alert the user of the security breach, as it is happening. If the user is on their iPhone or MacBook and they get a notification, they can try and quickly change their password, but more often than not, this will be too little too late. Ultimately, the only way to prevent your iCloud account from being compromised is to have a good password, hard security questions, and the two-step verification in place
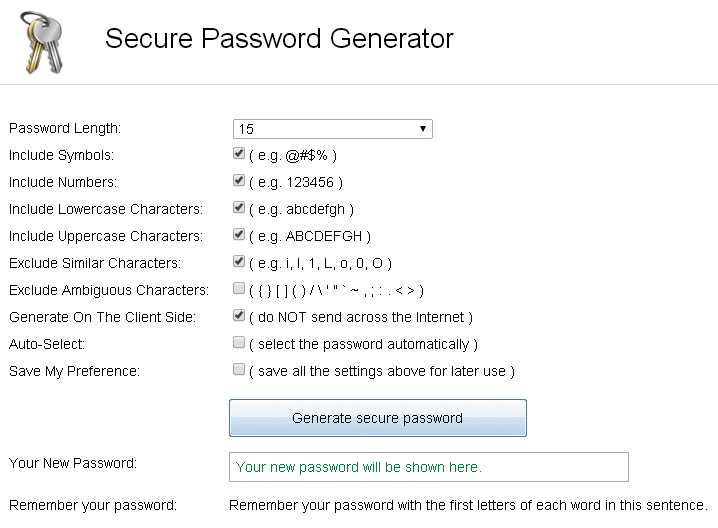
This recent scandal is part of a larger debate surrounding password security, and how to keep your various accounts secure. Many services, including Apple, require your password to have at least eight characters, an uppercase and lowercase letter and a number. Some services go even further and suggest using a symbol as well. Obviously, avoid passwords that contain personal information like family members’ names, favourite colour, pets, anything like that. Microsoft suggests that you shouldn’t even use actual words, and that all your passwords should be different. Google make an interesting point about remembering your passwords – just write them down. A complex password discretely-scribbled, well-hidden at the bottom of a drawer is much safer than a basic password that could be guessed by anyone in the world. Hackers generally work from behind a computer screen and don’t rifle through your home. When it comes to security questions, think in the same way – don’t pick obvious answers. If you have to choose from a preset list of questions, like ‘memorable place’, pick something obscure that you can still remember when asked, but that others wouldn’t know. In short, don’t pick your hometown. If you can write your own security questions, even better. If you’re at a loss over what to choose as your password, you can try using one of the many password generators available online, like https://strongpasswordgenerator.com/, http://passwordsgenerator.net/, or https://lastpass.com/generatepassword.php.
Cloud storage services like iCloud are really great tools to be utilised, and you should by no means give up using them because of this recent security scandal. You needn’t even stop your photos automatically uploading to your iCloud photostream – although if you did want to do that, you can disable this feature in settings>photos and camera>my photo stream. What you should do, though, is make your account as secure as possible. Use unique passwords for every account, obscure security answers, and take advantage of the two-step verification where it’s available. It might be slightly more hassle, but it can make the difference between keeping your data safe or leaking.